Microsoft accidentally leaks unpatched wormable exploit in SMBv3 protocol
Microsoft has accidentally leaked details on vulnerability in its SMBv3 protocol during their Patch Tuesday info. SMB stands for Server Message Block that is a protocol used for sharing access to files, printers and other resources on the network.

Most likely Microsoft planned to release the patch for the CVE-2020-0796 flaw since it was included in the Microsoft API for the March 2020 Patch cycle. Unfortunately, the fix was not released and there is no release date yet.
Security researchers from Fortinet explained that an unauthenticated attacker can possibly exploit this flaw to remotely execute arbitrary code within the context of the application. If exploited properly this vulnerability can make systems open to a “wormable” attack, meaning that it could easily spread between machines.
SMB is the protocol that was exploited by widely spread WannaCry and NotPetya ransomware viruses. Luckily no exploit code for CVE-2020-0796 has been released yet.
Affected Windows versions of the CVE-2020-0796 vulnerability include Windows 10 v1903 and v1909 and Windows Server v1903 (Core edition) and v1909 (Core edition).
Until the patch is released Microsoft recommends disabling SMBv3 compression on Servers with the following Powershell command:
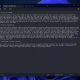
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” DisableCompression -Type DWORD -Value 1 -Force
Along with this a TCP port 445 on the enterprise perimeter firewall should be blocked. TCP port 445 is used to initiate a connection with the affected component.
Microsoft urges customers to install the updates for this vulnerability as soon as they become available.