New Trojan executes when hovered over a Powerpoint link
It seems that Hackers found a new way for spreading malware on Windows machines. A new malware will be installed on your machine even if you just hover over the powerpoint presentation file link. No macros, visual basic or Javascript is required for activation of this malware.
The file in question is a Powerpoint presentation file that potential victims receive as a file attachment in emails. Subject line usually contains the following lines: “RE:Purchase orders #69812” or “Fwd:Confirmation”. The name of the file is order&prsn.ppsx”, “order.ppsx”, or “invoice.ppsx”. Infected file may also be packed in the .zip file.
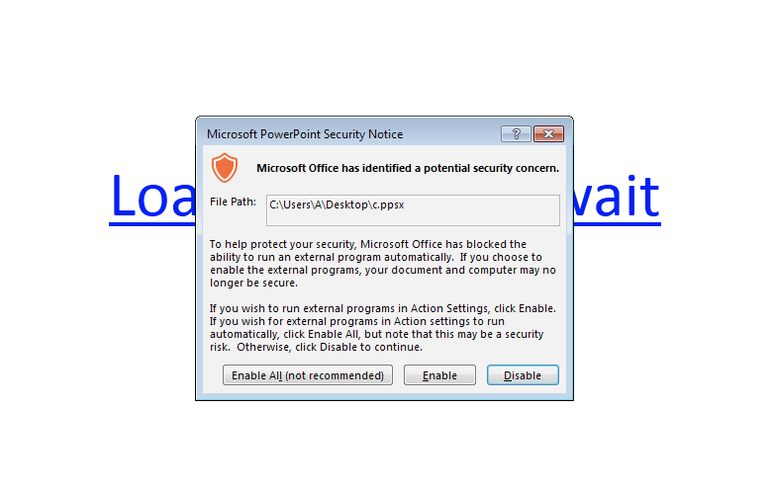
This method was used in spam campaigns in order to install a bank-fraud backdoor also knows as Gootkit, Zusy or Otlard. A PowerShell tool is invoked once the target hovers over the embedded hyperlink in the attached Powerpoint file and installs the malware. Users that are using the newer versions of Microsoft Office (2010 and above) should receive a warning because of the Protected View feature (picture below). Protected View is a read-only mode where most editing functions are disabled.
Spam campaigns with malicious contents can spread rapidly, but for now, the success rate for this hover technique is still unknown.If only half percent of internet users would activate this malware, it would pose a huge security threat to many organizations and, individual users, especially if those users are using the older versions of Microsoft Office.
In order to avoid infection with this malware Microsoft suggests using the Protected View, that should be enabled by default, especially for the files downloaded from the internet.